A simple, easy to understand guide to daily use of Microsoft Teams for maximum collaboration and productivity.
Archiv der Kategorie: Allgemein
ADFS 2012 R2 now supports Password Change (not reset) across all devices – samueld
Enabling Change Password in ADFS
By default, this functionality is disabled in ADFS. Change password looks just like another endpoint in ADFS and all you need to do is enable the endpoint. You can use the MMC snapin to enable this.
You can also do this via PSH using the Set-AdfsEndpoint cmdlet.
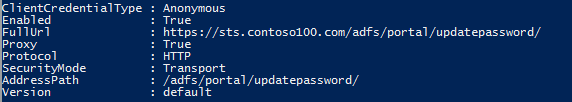
Once enabled, users can always access the change password page via https://adfs.contoso.com/adfs/portal/updatepassword/. It would look like this
Quelle: ADFS 2012 R2 now supports Password Change (not reset) across all devices – samueld
Update Send Connector SSL Certificate for Hybrid Configuration – The TexMX Record
This was because the on-premises send connector to Office 365 was still configured to look for that expired certificate (which had also been deleted already).
The fix was to perform the following:
- Open Exchange Management Shell on the on-premises Exchange server
- Run Get-ExchangeCertificate, and note the Thumbprint of the correct certificate to be used.
- Run $cert = Get-ExchangeCertificate -Thumbprint <thumbprint>
- Set a new variable and assign it the concatenated values of the Issuer and Subject values of the certificate (must also include <I> and <S> before each field):
$TLSCert = (‘<I>’+$cert.issuer+'<S>’+$cert.subject) - Update the send connector with the new values
Set-SendConnector -Identity “Send Connector Name” -TLSCertificateName $TLSCert
After completing this, any queued mail destined for the Office 365 tenant should begin flowing
Quelle: Update Send Connector SSL Certificate for Hybrid Configuration – The TexMX Record
have i been pwned? Test all users of your domain
Aus einem Powershell-Beispiel von „IT Pro blog“ weiterentwickelt
https://infracloud.wordpress.com/2015/10/29/have-you-been-pwned-use-powershell-to-find-out/
Get-Pwned.ps1
Import-Module „C:\adm\custom\BasicTools.psm1“
$Global:CheckURI = „https://haveibeenpwned.com/api/v2/breachedaccount“
$global:OutputPath = „C:\“
$global:results = @()
Function ValidateAddress($Emailaddress){
try{
$Request = Invoke-WebRequest -Uri „$global:CheckURI/$Emailaddress“
$Response = ConvertFrom-Json $Request
Return $Response
}
catch [exception]
{
Return $null
}
}
Function IsValidEMail($email){
$EmailRegex = ‚^[_a-z0-9-]+(\.[_a-z0-9-]+)*@[a-z0-9-]+(\.[a-z0-9-]+)*(\.[a-z]{2,4})$‘;
return ($email -match $EmailRegex)
}
Function IsValidDomain($mailaddress){
$domain = $mailaddress.Substring($mailaddress.IndexOf(„@“)+1)
$obj = Get-AcceptedDomain -Identity $domain -ErrorAction SilentlyContinue
if ($obj -eq $null){
$result = $false
}else{
$result = $true
}
return $result
}
Function ConvertHaveibeenpwnedObject($obj,$mailaddress,$username){
Set-ToolsLogAddLine -LogTXT „Compromised account $username, $mailaddress“
$result = New-Object -TypeName PSObject
$result | Add-Member -MemberType NoteProperty -Name username -Value $username
$result | Add-Member -MemberType NoteProperty -Name mailaddress -Value $mailaddress
$result | Add-Member -MemberType NoteProperty -Name HIBPAddedDate -Value $obj.AddedDate
$result | Add-Member -MemberType NoteProperty -Name HIBPBreachDate -Value $obj.BreachDate
$result | Add-Member -MemberType NoteProperty -Name HIBPDataClasses -Value ([system.String]::Join(„;“,$obj.DataClasses))
$result | Add-Member -MemberType NoteProperty -Name HIBPDescription -Value $obj.Description
$result | Add-Member -MemberType NoteProperty -Name HIBPDomain -Value $obj.Domain
$result | Add-Member -MemberType NoteProperty -Name HIBPIsSensitive -Value $obj.IsSensitive
$result | Add-Member -MemberType NoteProperty -Name HIBPIsVerified -Value $obj.IsVerified
$result | Add-Member -MemberType NoteProperty -Name HIBPLogoType -Value $obj.LogoType
$result | Add-Member -MemberType NoteProperty -Name HIBPName -Value $obj.Name
$result | Add-Member -MemberType NoteProperty -Name HIBPPwnCount -Value $obj.PwnCount
$result | Add-Member -MemberType NoteProperty -Name HIBPTitle -Value $obj.Title
return $result
}
Function main{
Set-ToolsLogCreate -LogFilePath „C:\adm\custom\logs\“ -LogPrefix „CompromisedAccounts“
Remove-ToolsLog -olderThenDays 21
Set-ToolsLogAddLine -LogTXT „Collect accounts“
$users = Get-ADUser -LDAPFilter „(mail=*)“ -Properties mail, proxyaddresses -ResultSetSize $null
$i = ($users).Count
Set-ToolsLogAddLine -LogTXT „Test $i accounts“
$i = 0
foreach($user in $users){
$i ++
if($i/100 -is [int]){Set-ToolsLogAddLine -LogTXT „$i accounts tested“}
$proxymail = „“
$usermail = „“
$usermail = $user.mail.ToLower()
$output = „“
if (IsValidEMail($usermail)){
if (isValidDomain($usermail)){
$obj = ValidateAddress($usermail)
if ($obj -ne $null){
$global:results += ConvertHaveibeenpwnedObject -obj $obj -mailaddress $usermail -username $user.SamAccountName
}
}
}
Foreach($proxyAddress in $user.proxyaddresses){
$proxymail = $proxyAddress.ToLower()
if ($proxymail.StartsWith(„smtp:“)){
$proxymail = $proxymail.Substring($proxymail.IndexOf(„smtp:“)+5)
if (IsValidEMail($proxymail)){
if ($proxymail -ne $usermail){
if (isValidDomain($proxymail)){
$obj = ValidateAddress($proxymail)
if ($obj -ne $null){
$global:results += ConvertHaveibeenpwnedObject -obj $obj -mailaddress $usermail -username $user.SamAccountName
}
}
}
}
}
}
}
Set-ToolsLogAddLine -LogTXT „Finish“ -foregroundcolor „green“ -backgroundcolor „darkgray“
$global:results | Export-csv „$global:OutputPath\CompromisedAccounts.csv“
}
main
use log parsing for MS
use LogExpert or LogParser to analyse logs of Exchange or other Microsoft products
LogExpert
https://logexpert.codeplex.com/releases/view/610775
LogParser
http://www.microsoft.com/en-us/download/details.aspx?id=24659